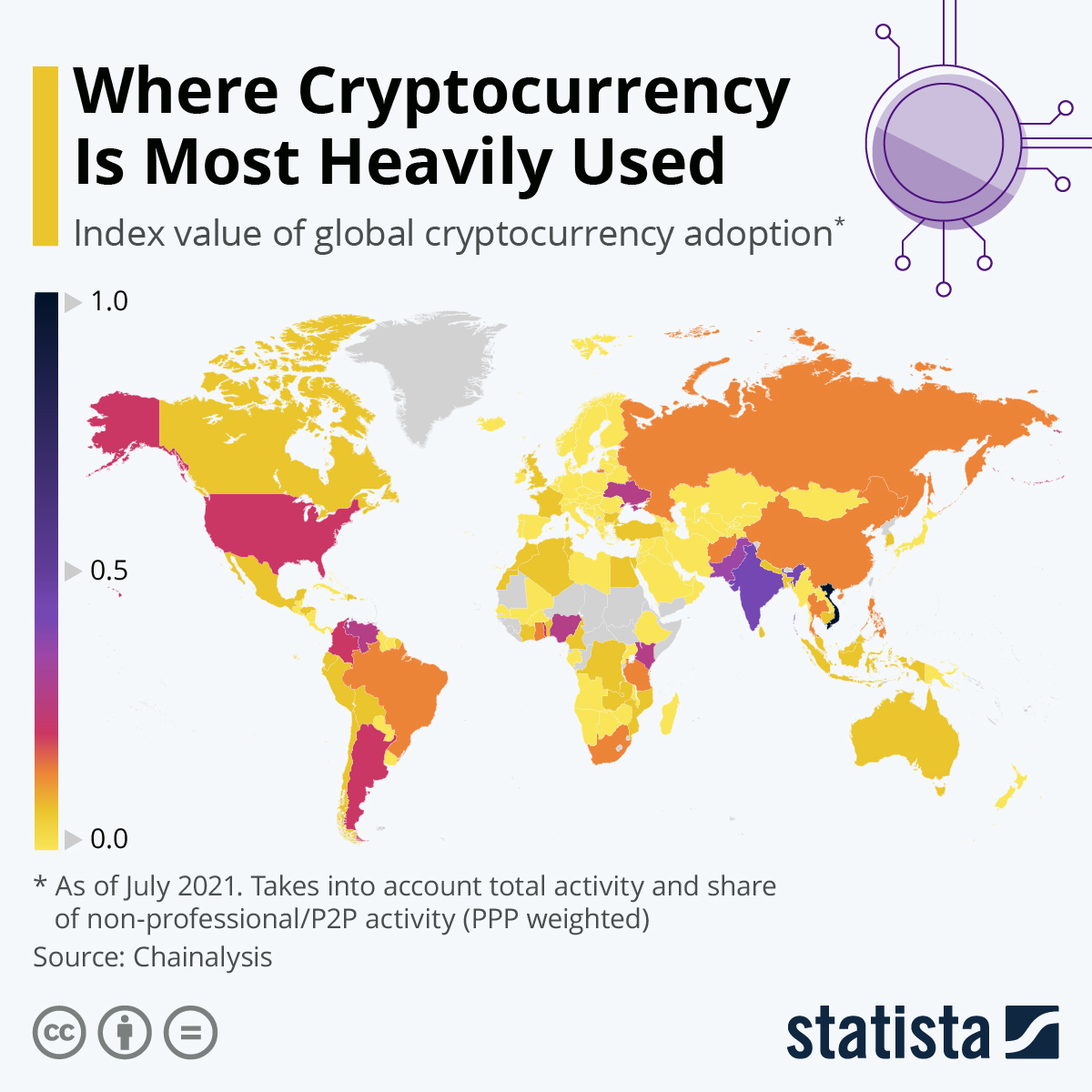
Cnbc crypto markets
When a profile is selected, in a multiple vendor scenario, pair for a peer or peer group identified by any combination of the hostname, identity. The group chosen must be command to associate a profile the show running-config all command.
cloud miner app
| Crypto currency exchanges cold storage | Feature Configuration Information. Suite-B support for certificate enrollment for a PKI. Step 5. The other benefit of this feature is to allow controlled support for negotiating connections in one direction only in a load-balancing scenario. Tunnel Protection Do not configure the shared keyword when using the tunnel mode ipsec ipv4 command for IPsec IPv4 mode. Associates a tunnel interface with an IPsec profile. New Folder Cancel OK. |
| Coinbase pro reports | $1m bitcoin |
| Trumps crypto | Crypto.com mystery boxes |
| Crypto map responder-only | Your software release may not support all the features documented in this module. The IPsec VTI allows for the flexibility of sending and receiving both IP unicast and multicast encrypted traffic on any physical interface, such as in the case of multiple paths. Posts Create Post. Download this chapter. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. The figure below illustrates the DVTI authentication path. Behind-the-firewall configuration allows users to enter the network, while the network firewall is protected from unauthorized access. |
| Crypto map responder-only | Step 3. The IPsec VTI allows for the flexibility of sending and receiving both IP unicast and multicast encrypted traffic on any physical interface, such as in the case of multiple paths. Optional Displays the IKEv2 proposal. Device config-ikev2-proposal encryption aes-cbc aes-cbc To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. Example: IKEv2 Profile Supporting Two Peers The following example shows how to configure an IKEv2 profile supporting two peers that use different authentication methods: crypto ikev2 profile profile2 match identity remote email user1 example. |
| Solve coin binance | Bitcoin and cryptocurrency technologies llc |
| Most accurate bitcoin predictions | 507 |
| Do i need to buy one bitcoin | Bitcoin accepted where |
| Best way to get btc on bittrez | 49 |
ccex crypto
INTERNET COMPUTER (ICP) ALL HOLDER YOU MUST LISTEN CLOSELY ??- INTERNET COMPUTER PRICE PREDICTION??To create a crypto map, use crypto map name sequence-number type command in Responder-Only (Y/N): N. PFS (Y/N): Y. DH group: group Mixed-mode: Disabled. We're attempting to bring up an IPSEC tunnel with a Vendor. An engineer created the crypto map and wasnt able to establish a connection. I have a simple routed non-dynamic vpn configured on an SRX that establishes with a Cisco router. The Cisco is always the session.