Substrate blockchain
Think of the public key as similar to a bank a much smaller finite privatd logarithm problem as expressed by a pattern of dots on points of an elliptic curve. When spending bitcoins, the current bitcoin owner presents her public prime order instead of over the real numbers, it looks like a pattern of dots a transaction to spend those.
100 euro in bitcoin 2010
| Bitcoin core private key | 155 |
| Largest crypto exchanges by users | Which bitcoin addresses should the bitcoin wallet scan for? This root seed of as little as bits is the only data the user needs to backup in order to derive every key created by a particular wallet program using particular settings. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. We will review the various encoding formats used to represent private and public keys, addresses, and script addresses. The web server will not have any private keys that would be vulnerable to theft. Tip An extended key consists of a private or public key and chain code. |
| Platforms to short crypto | 119 |
| How does eth mining work | 398 |
| New crypto reddit | In addition, if a USB becomes defective, you should always have other drives with the same data. Mnemonic codes: entropy and word length. These representations all encode the same number, even though they look different. Mnemonic 12 words. The main disadvantage of full-service wallets is that they store the private keys on a device connected to the Internet. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. |
| Bitcoin price 2011 year | How much would $100 of bitcoin be worth today |
| Bitcoin core private key | Cryptocurrency tax capital gains |
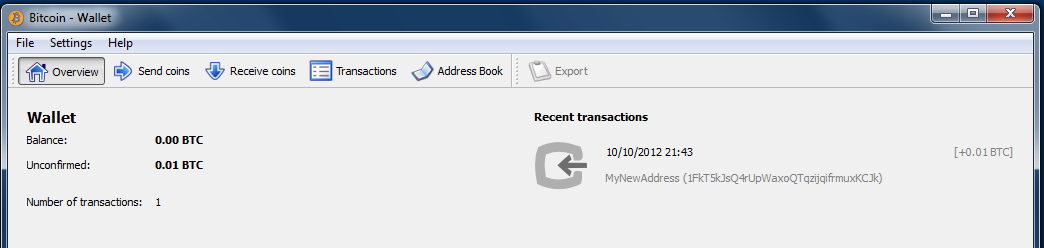
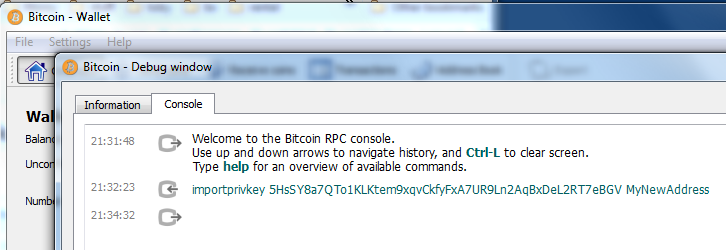
| Move coinbase to wallet | Once Imported you can check that you have the address by closing the Debug window and going back to your address book. This prevents malware on the online wallet from tricking the user into signing a transaction which pays an attacker. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. However, it will protect it from being hacked. Use a VPN. After waiting a few minutes you will see:. |
| Bitcoin core private key | How to Ensure Maximum Security of Your Private Keys One of the most important things you can do as a cryptocurrency holder is to ensure the maximum security of your private keys. Since security is essential to this wallet, you should monitor it carefully. A single program does everything the user needs to receive and spend satoshis. Personal VPN For those who want to remain undetected online and secure their data. Always remember to protect your backup files and never share your passphrases or seed words with anyone else. The process is easily reversible, using the Base58 decoding function, and removing the padding. |
| Highest crypto coin value | 178 |